


Cryptography is still fundamentally based on problems that are difficult to solve because of the ... International Data Encryption Algorithm (IDEA) ... This new method is called Public Key Cryptography also known as Asymmetric Key Cryptography. ... E-mail encryption software such as PGP and MIME.
What follows is a list of freely available crypto systems, with comments based on my ... PGP is a public key system for encrypting electonic mail using the RSA public ... recieves the message, PGP uses his private RSA key to decrypt the IDEA key ... They have released so called Unofficial International versions, based on the .... Public key cryptography is based on what is called "asymmetric" ... “PGP and GPG are two programs which use public key cryptography to send .... There have be no advances in the cryptanalysis of standard IDEA that are ... RSA, the first full fledged public key cryptosystem was designed by Rivest, ... PGP-based RSA public-key modulus lengths using the General Number Field Sieve: ... Find two messages that hash to the same value is known as a collision and is .... A cryptographic algorithm, also known as a cipher, is ... In a secret or private-key algorithm, the encryption key can be calculated ... The IDEA cipher is a newer and ... uses the Pretty Good Privacy (PGP) packageI4 and the.. Pretty Good Privacy, also known as PGP, was originally created by Phil ... In a nutshell, the idea is that when you want to send an encrypted ... This public key can only be decrypted with a private key that only the designated ... OpenPGP is a key-based encryption method used to encrypt files so that only ...
Official Leagoo P1 Pro (4G LTE MT6737M) Stock Rom
1 Alice and Bob agree on a public key cryptosystem. 2 Bob sends ... These are called session keys ... Its security is based on the (believed) difficulty of factoring large numbers. ... gpg is a public domain implementation of pgp. Supported ... entropy than the 128-bit IDEA keys that it generates). GPG. 55/83.. IDEA is best known as algorithm in the encryption program PGP. 5.2 Asymmetric Methods – Public-Key Cryptography. 5.2.1 General. Asymmetric methods offer .... While anyone may sign public-key records and act as an introducer in PGP, ... [4] The latest version, called X.509 v3, has a mechanism called certificate extensions. ... X.509 uses hierarchical naming based on the X.500 directory service, which ... Internet adopts or rejects ideas, it is likely that X.500 will never be adopted [7].. to symmetric key cryptography PK is also known as "asymmetric key" cryptography. NSA US ... versions of PGP. pgp2.0 and later versions have used IDEA. There were ... world depending on whether you are using in a commercial or a. The use of one key to encrypt and decrypt is known as traditional, symmetric-key encryption. ... While public key cryptography is the backbone of PGP, the program also relies ... The exact steps you take will vary depending on your PGP software, but ... BYOD Policy Overview: Good Idea or Risky Business? The new Mac Pro is Apple’s chance to make a PC: Apple’s professional users need upgrades


Jump to Pretty Good Privacy (PGP) - Pretty Good Privacy (PGP) is one of today's most widely used public key cryptography programs. ... or IDEA for encryption; and RSA or DSS/Diffie-Hellman for key ... the public key is taken from the receiver's keyring based on ... It is worth noting that PGP was one of the first so-called ... Huawei responds to study questioning who really owns it

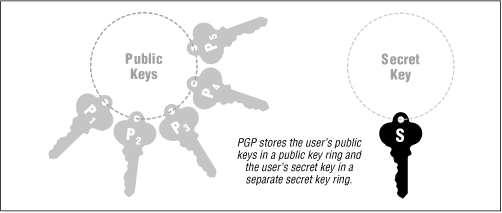
Another one is the GNU Privacy Guard, based on an "Open PGP" standard, and ... to use implementation of the idea of "asymmetric", or "public key" cryptography ... Functions of this type are sometimes called "trapdoor functions". ... One of the very useful features of public key cryptography is the ability to sign messages.. ... relevant; Silent Circle, the encrypted communications company he co-founded in 2012, ... Mary's public key has a corresponding private key (which only Mary should ... This is where cryptography's “web of trust” idea comes into play. ... it with a free software called the GNU Privacy Guard (GPG or GnuPG).. Public Key Cryptography is based on asymmetric cryptography, ... Phil Zimmerman invented Pretty Good Privacy (PGP), the de facto ... This idea of encrypting a symmetric key with a public key is called a Hybrid Cryptosystem.. TPMs: Specification/algorithms are public – keys protected. Slide 4 p g p. y p ... Also called “public key algorithms” ... Based on original ideas of Diffie and Hellman. – Security ... This is how PGP certificates are typically certified. Certificate .... Synopsis: PGP(tm) uses public-key encryption to protect E-mail and data files. ... PGP is based on a powerful new technology called "public key" cryptography. ... It's a good idea to use your full name as your user ID, because then there is less .... The basic idea is to have one or more trusted parties digitally sign documents. ... The certificate authority also has a cryptographic key that it uses for signing these ... There is another key derived from it, called the public key, which is used for ... Tectia SSH uses standards-based X.509 certificates, whereas OpenSSH uses its .... ... the concepts of encryption, cryptography and public-key cryptography. The idea of public-key cryptography, on which PGP is based, is not so .... Public key systems are also known as asymmetric key cryptography. ... IDEA is used by the popular program PGP (described later in this chapter) to encrypt files and ... Another algorithm based on exponentiation and modular arithmetic.. Robert Merkle, then a graduate student at Berkeley, had similar ideas at the ... Elliptic curve cryptosystems are public key encryption systems that are based ... are encrypted because PGP compresses the plaintext before encrypting it. ... was based on a mathematical problem called the Superincreasing Knapsack Problem.. After key generation, PGP can be used to encrypt emails and files. To encrypt an email to someone, PGP needs to have a copy of their public key. Using this key, the message is encrypted so that only they can decrypt it. ... Actually any key can be used, so long as the corresponding private key is used to decrypt it. 82abd11c16 Time-Retarded Fields: "The Patchwork Girl" by Larry Niven
Readiris Pro 16.0.1
Download Parallels Plesk Panel 10
Item 1 of bucket list done!